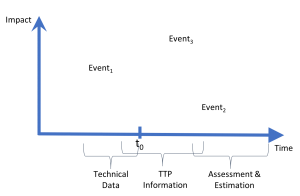
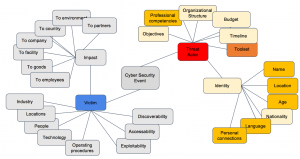
In the previous post, we addressed the importance of being able to parse the indications from the feed.
In order to match indications with external origin, you must have baselined you internal operations for the categories that interest you.

Let’s say you receive a report that suspected Guatemalan state-sponsored actor known as Sunshine Donkey (AKA Daft Burro / AKA Yummy Burrito) wiped hard drives at the Monterrey, Mexico facility of The Salsa Inc., a Mexico-based agri-food business, presumably in retaliation for Mexico’s policy to charge Guatemalan nationals higher rates for scuba diving permits.
The report includes malware file hashes.
The first thing your mega heavy cyber intel provider will have you do is grab the hashes and search your sensors. No hit = no problem. You are safe. Right?
Wrong.
A forward-looking approach would prompt you to ask the following questions as you attempt to match the external event against your own operations:
- Do any of the countries where I operate have ongoing scuba permit disputes with Guatemala?
- How easily could the same attack techniques be used to wipe my hard drives?
- Do I have any dealings with The Salsa Inc?
- Do I have any dealings in agri-foods?
- Do I have any facilities in Monterrey?
- Do I have any facilities in Mexico?
- Do I have Mexican suppliers (in this industry)?
- Do I have Mexican customers (in this industry)?
- Do I have any dealings in scuba?
- Do I have Guatemalan suppliers or customers (in this industry)?
- Do my key employees have plans to scuba dive in Mexico in the near future?
Now we are getting closer to proactive cyber risk intelligence. The key is to prepare to answer these questions before you get the report. More on that next time.