Our previous posts established the groundwork for understanding how cyber risk intelligence allows organizations to answer the question “When will my organization be the victim of a significant cyber incident?”
When we last left off, we agreed to discuss four ways cyber risk intelligence analysts could match external or “threat” developments with internal systems the analyst desires to protect:
- Technical Data
- Tools, Techniques, and Procedures (TTPs)
- Assessment and Estimation (A&E)
- Vulnerability Discovery and Disclosure Data
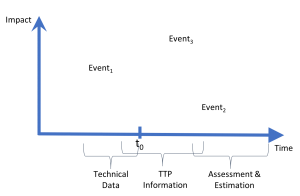
To give you an idea of how each of these contributes to our objective of anticipating cyber incidents, I have labeled first three of them on the X axis of the Boom Chart.
You notice that Technical data is primarily reactive. It is generally gleaned from incident investigation.
TTPs are also learned from previous attacks, but carry forward due to the insight they provide about how an adversary operates.
Assessment & Estimation is forward looking based on a broad variety of factors that extend beyond bits and bytes level analysis.
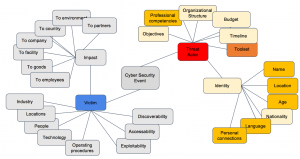
The following image of the mind map (discussed previously) is color coded to indicate which elements fall under each category.
While this mind map is somewhat notional rather than complete and detailed: brown represents technical data, yellow represents TTPs, and beige represents estimation and assessment.