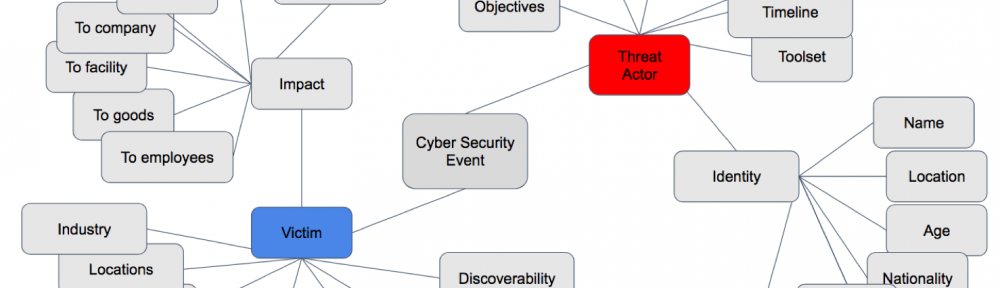
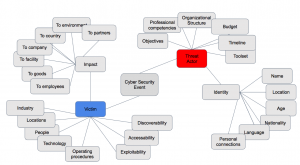
The cyber risk intelligence analyst can use several techniques to place events and impacts accurately on the boom chart.
He must start with a foundational understanding of cyber event elements, many of which display in the following mind map:
An intelligence analyst learns all he can about these items. He is fascinated by context, and terrified by ignorance. He explores relationships and advances hypothesis. He builds on his knowledge and previous estimations. A good analyst knows and readily applies a broad number of analytical techniques, asking question after question — carefully documenting his results — building histories and frameworks.
When trying to anticipate the future, the cyber risk analyst applies all his efforts to match what he knows about the external environment with what he knows about the internal environment he must protect.
We can divide intelligence product types useful in this “matching” effort into four broad categories:
- Technical Data
- Adversary TTPs
- Assessment and Estimation
- Vulnerability Discovery and Disclosure
In the following posts we will look at each of these in greater detail.