So, a friend of mine, Tyler Klingler, came across an interesting article about the control system technology at AT&T field, home of the San Francisco Giants, and venue of the several World Series games.
One of the photos in the article featured a nice screen shot of Toro “Golf Vision”, as used by some part of the Subair system. Subair is basically a vacuum beneath the field to keep the soil just right for hardball. Cool huh?
Here’s the linked image:

Image by Dusty Trayer as posted to TechHive
Tyler is quite observant — actually, he’s one of the most observant people I know. He was looking at the image, and noted it had good resolution. He zoomed in on the screen just because.
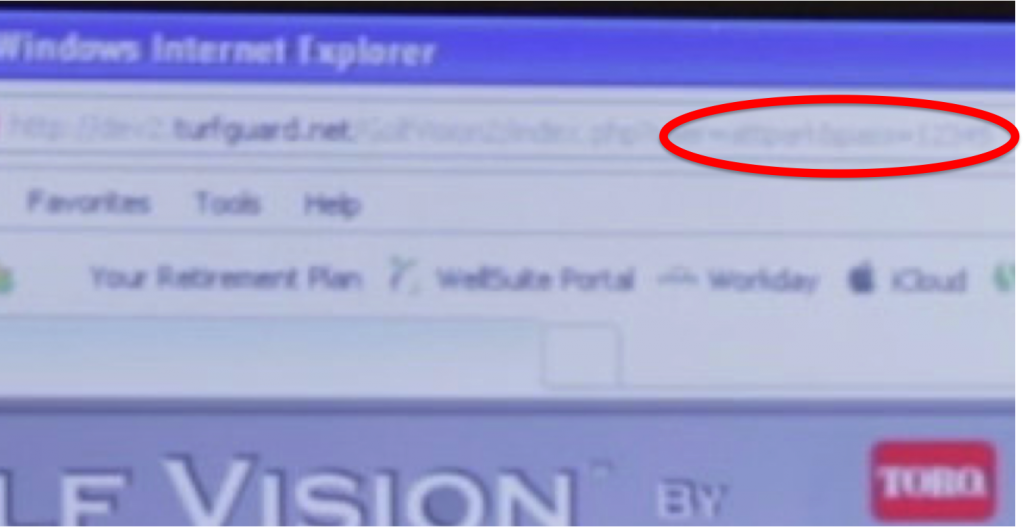
What he found was interesting: Username and password in the URL. Check it out:
Ok, it requires a little creativity and deductive reasoning to get the username, but the password is five characters long, starts with 1 and ends with 5.
Given the URL, the application is obviously a Web app. So any observant reader of TechHive can now log in.
Tyler reached out to what appeared to be appropriate contacts at the stadium and the Giants, but received no response.
What could an attacker do? Well, Online manuals make it seem that an attacker could view the moisture sensor readings, and maybe change some configurations — but it does not seem possible to turn on the sprinklers to coincide with the 7th inning stretch!
So is it a big deal? Probably not, but there could always be opportunities to pivot. Maybe cross site scripting against the ground keeper’s browser would result in access to those sprinklers after all…
But to make matters worse, it looks like the Toro Golf Vision Web app: 1) passes the creds to its Web server in the clear and 2) doesn’t actually allow the user to reset a password — that’s only done when you register/sign up [See the manual, page 3].
Lessons learned:
- Beware of insecure IOT apps
- “No ICS screenshots!” is a solid policy