I thought this was pretty big news:
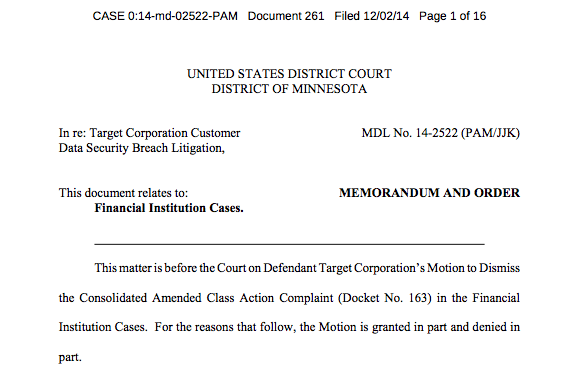
“Judge rules that banks can sue Target for 2013 credit card hack”
Here’s the key quote from the actual decision:
Plaintiffs have plausibly alleged that Target’s actions and inactions—disabling certain security features and failing to heed the warning signs as the hackers’ attack began—caused foreseeable harm to Plaintiffs. Plaintiffs have also plausibly alleged that Target’s conduct both caused and exacerbated the harm they suffered. And Plaintiffs’ allegation that Target was solely able and solely responsible to safeguard its and Plaintiffs’ customers’ data is also plausible. Imposing a duty on Target in this case will aid Minnesota’s policy of punishing companies that do not secure consumers’ credit- and debit-card information.
I was particularly interested in “failing to heed the warning signs” part. As an intelligence professional, I have always found wisdom in the statement “willing ignorance is negligence”. Now we have a case where in the cyber world that may ultimately ring true.
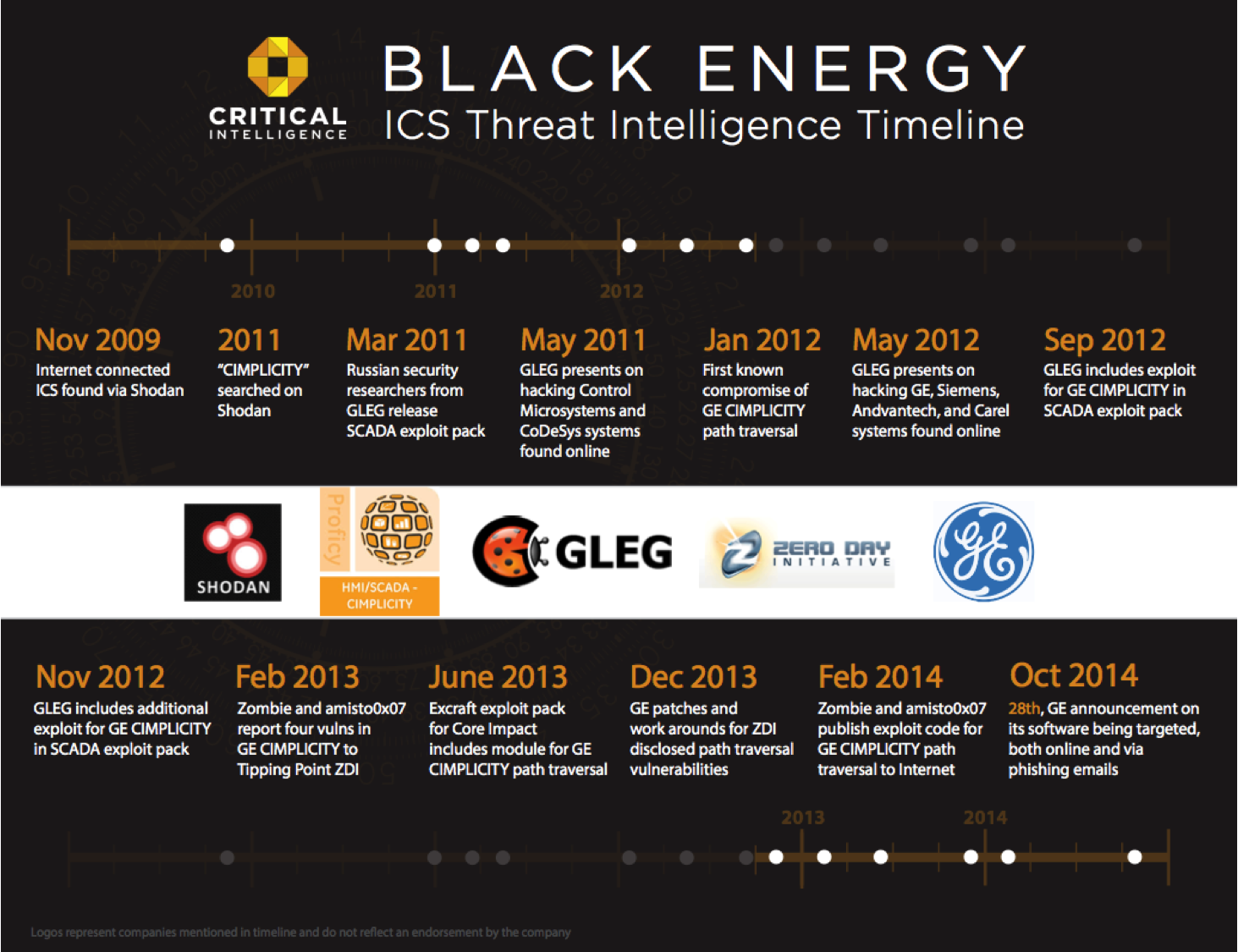
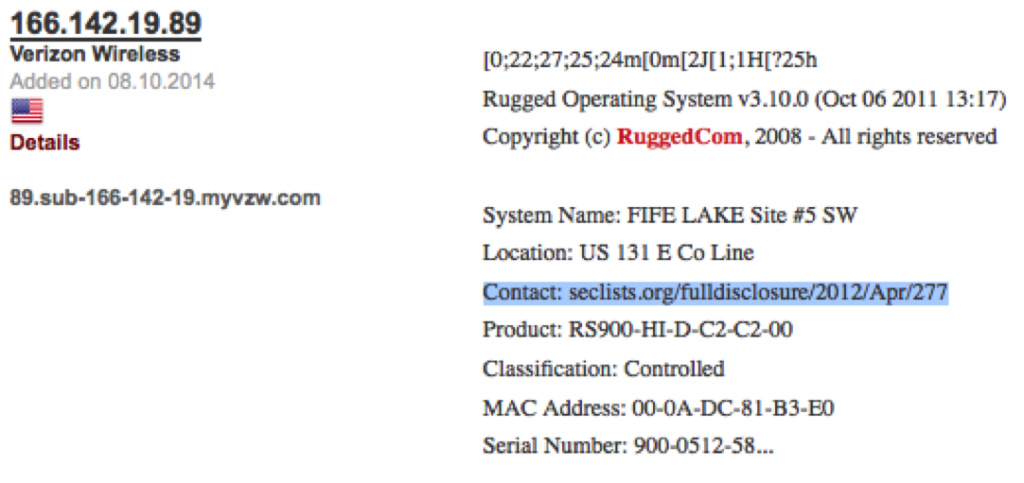
Pointing to possible implications for critical infrastructure, we might consider Internet-connected ICS, including engineering lap tops with access to Web and Email. We have numerous documented cases where these configurations have led to compromise (see Havex and Black Energy).
If one of these led to real physical damage, I imagine the law suits would fly (assuming of course that the “cyber” cause could be accurately ascertained).
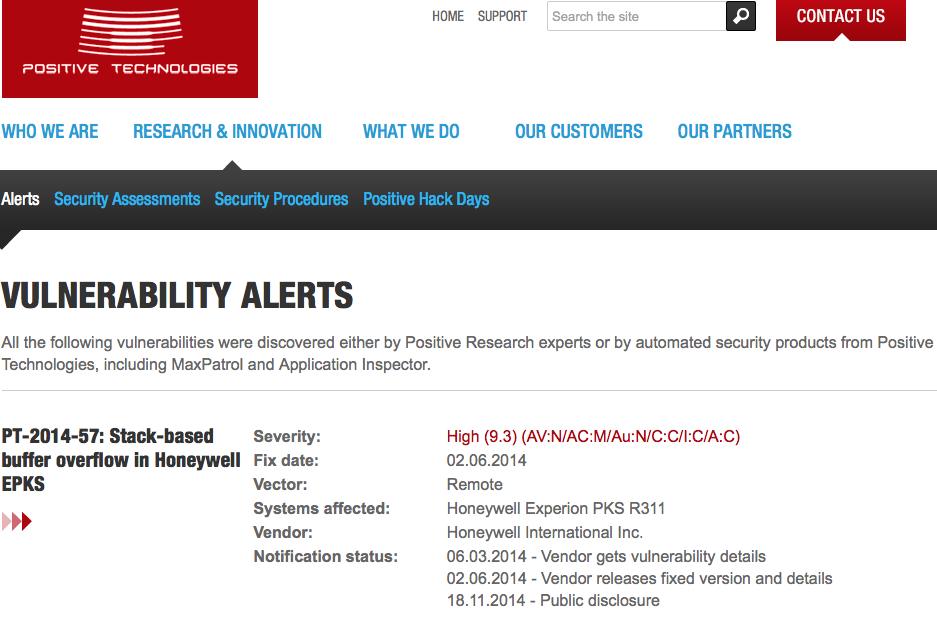
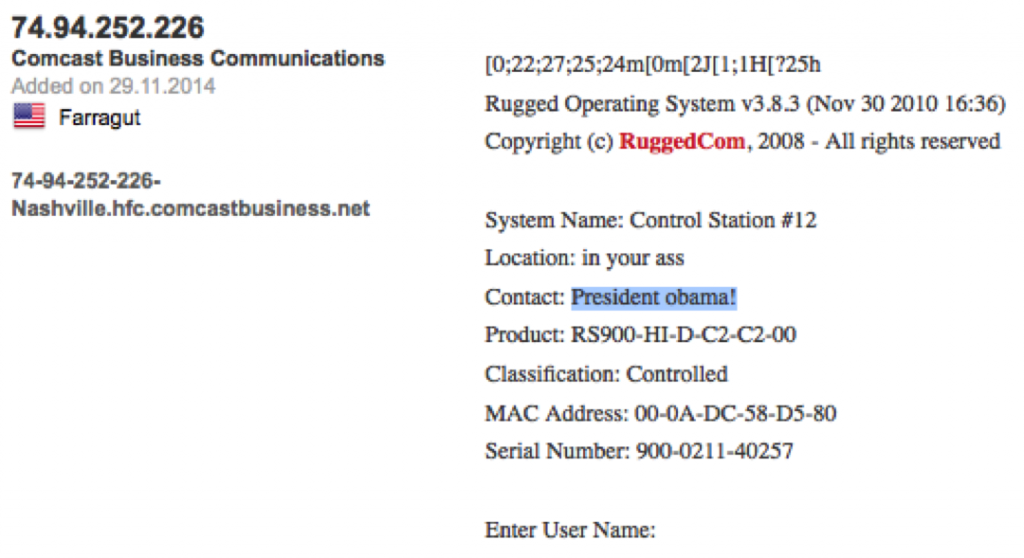
After five years of warning about the problems of connectering-up yer HMI to the public Internexus, I don’t think there should be much excuse for getting your plant compromised by anyone who can run a freely-available exploit tool (let alone by someone trying an unchanged default password!).
As a final note, and a point I’ve made before, to what extent should taxpayers be subsidizing incident response when then victim “failed to heed the warning signs”?