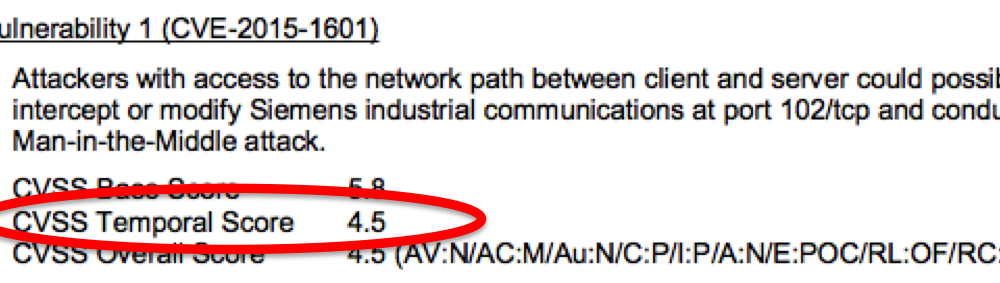
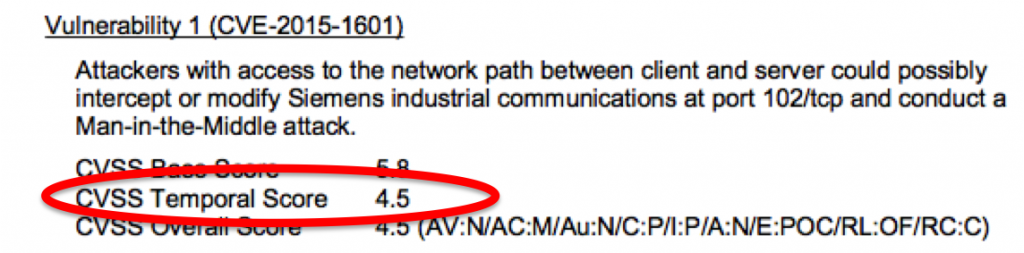
I recently realized (though they’ve been doing it for years) that in its vulnerability advisories, Siemens is calculating not only a CVSS base score, but is also including Temporal metrics. Temporal metrics are those “variables” that can change over time, including “Exploitability”.
Exploitability describes how easily/reliably an adversary can exploit a vulnerability. CVSSv2 official documentation describes:
This [Exploitability] metric measures the current state of exploit techniques or code availability. Public availability of easy-to-use exploit code increases the number of potential attackers by including those who are unskilled, thereby increasing the severity of the vulnerability.
Choices for Exploitability (per CVSSv2) include: Not Defined, Unproven that exploit exists, Proof of concept code, Functional exploit exists, and High.
Obviously, Exploitability scores can and do change over time (it’s a “temporal metric”). Essentially that means that someone might release exploit code for a vulnerability weeks, months, or even years down the road.
As mentioned above, Siemens includes temporal metrics in its vulnerability advisories. ICS-CERT does not include temporal metrics, but does include a section entitled, “Existence of Exploit”.
When producing a vulnerability advisory that includes information about the existence of an exploit, you have to be careful not to unintentionally mislead those relying on your advisory some time later.
For example, you would not want the user of a vulnerable ICS product (e.g. those operating critical infrastructure) to rely on your most-recent advisory (maybe at a yearly maintenance downtime) and conclude, based on the information in the advisory, that they can skip a patch because there are no known exploits — when in the intervening time, exploits have been released.
This makes me wonder whether Siemens and ICS-CERT are monitoring for exploits (be they free or commercial) against vulnerabilities AFTER advisories have been released, and whether they update the advisories accordingly.
Because exploit disclosures significantly alter the risk associated with a particular vulnerability, the Critical Intelligence Core ICS Intelligence Service provides continuous, ongoing, monitoring and alerting for ICS vulnerabilities AND exploits.