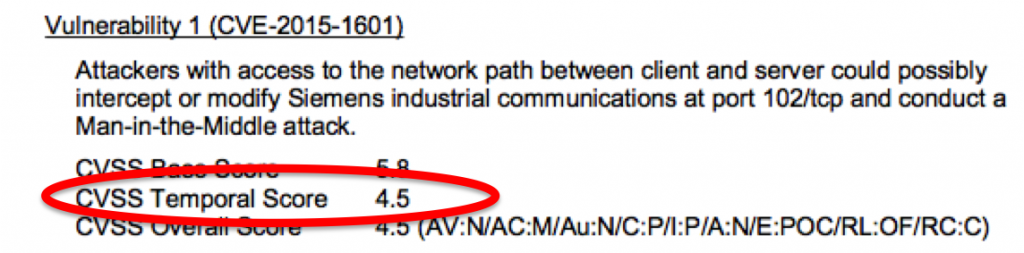
I read, with a sense of satisfied indignation, the headline “Obama’s info-sharing plan won’t significantly reduce security breaches… according to Passcode’s Influencer’s Poll“.

Not that the”influencers” know all, or that the poll couldn’t have introduced bias. But there appears to be a significant disconnect between what security leaders and practitioners believe and what the federal government is pushing.
It seems ridiculous. Why is this the case?
Here are my best guesses:
- 85% of Critical infrastructure is privately owned. Government has a duty to help, right?
- Historically, many private organizations only learned of breaches when officials from the federal government paid a visit to their corporate offices. Hence, leaders of these organizations believe that the government has some super secret technology that allows them to detect all attacks against the private sector. The government should just automate sharing of that information and problem solved.
- Private organizations aren’t going to turn down “free” (well taxpayer funded) assistance from some federal group who holds themselves out as “the experts”.
- Bureaucracy waxeth. Once government has private industry depending on it for “free” assistance, it can easily make the case that “the private sector loves it” and so it “just needs more funds” to scale up.
- Info sharing sounds easy. But it’s not: let’s not forget that someone has to actually create the information in the first place, that tools have to be created/deployed to consume it, and that analysts and practitioners must be trained to action it.
- It’s a dirty compromise. Industry can request info sharing to hold off government regulation. Legislators can easily point to information sharing to show they are addressing the issue.