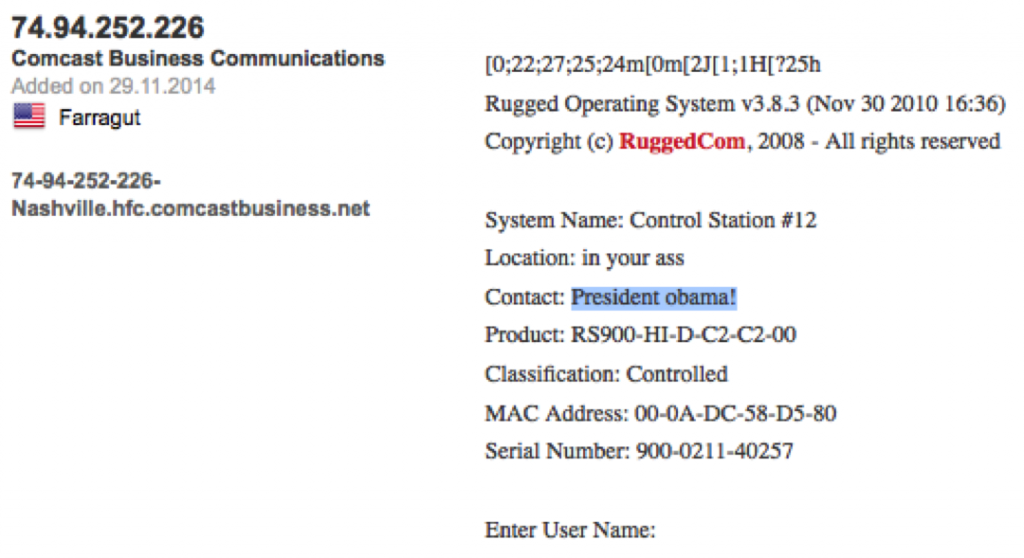
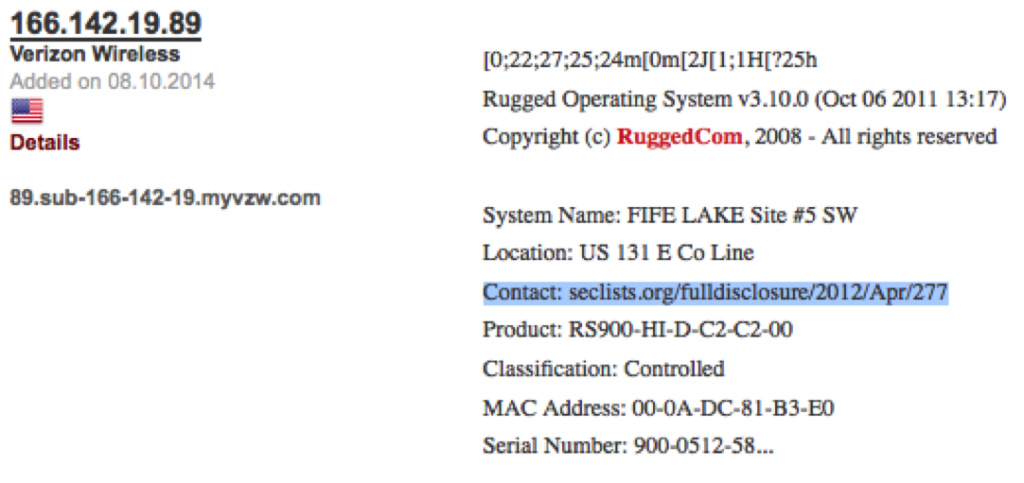
In my opinion, one of the most serious ICS bugs ever released was the RuggedCom authentication bypass vulnerability: CVE-2012-1803
It essentially allows users to connect to industrial-grade network devices if they know the MAC address. The MAC address is included by default on the Web server and in the Telnet response. If you get access to Telnet or HTTP, you pop the MAC address into a public script and you get the backdoor password.
I was browsing around Shodan the other day, and spotted what appear to be compromised Ruggedcom gear. How do I know they are compromised? Well look at the results and see for yourself:
So, while you might not hear about compromised ICS/SCADA everyday. Here are couple of examples that it is happening to the unaware.